Since APIC Release 2.2(1n) Cisco enabled a feature called Preferred Groups.
What does it and when do you need it?
It allows defined EPGs in a VRF still to communicate with each other even when the Policy enforcement is enabled and there are no contract between those EPG’s. This can be, for example, really useful for migration scenarios. You can use them with all kind of EPG’s: EPG, uEPG or External EPG.
But there are a few things you should be aware when you use it:
- You have to specify your external Subnet(s) or you won’t have external connectivity after you change the VRF to “Enforced”
- But you can’t use the 0.0.0.0/0 in the External Subnet for the External EPG, if you do you’ll end up with this error:
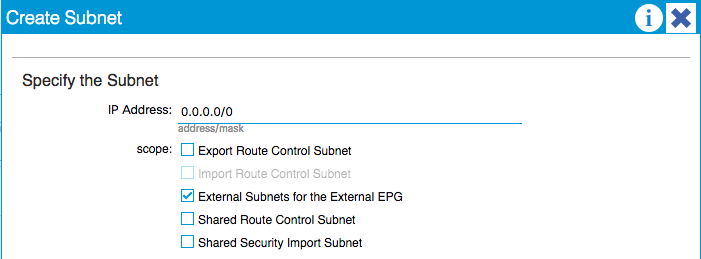
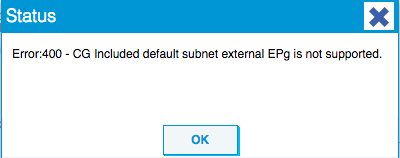
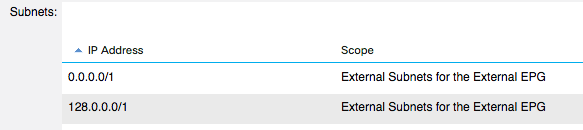
A solution for this is that you specify the external network(s) more closely or if you need the equivalent for the 0.0.0.0/0 you can do this:
So what is necessary to configure the preferred group?
First, you have to Enable it under Tenant->Networking->VRF->”Your VRF”->EPG Collection for VRF:
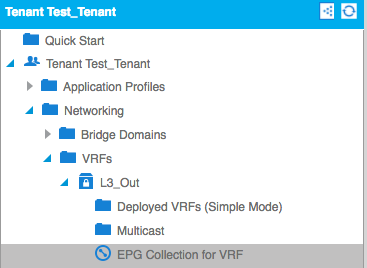
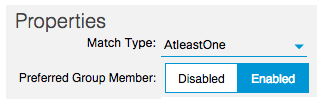
The next stept is to set the EPGs you’ll want to have to Include.
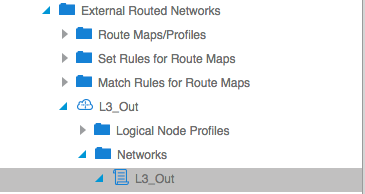
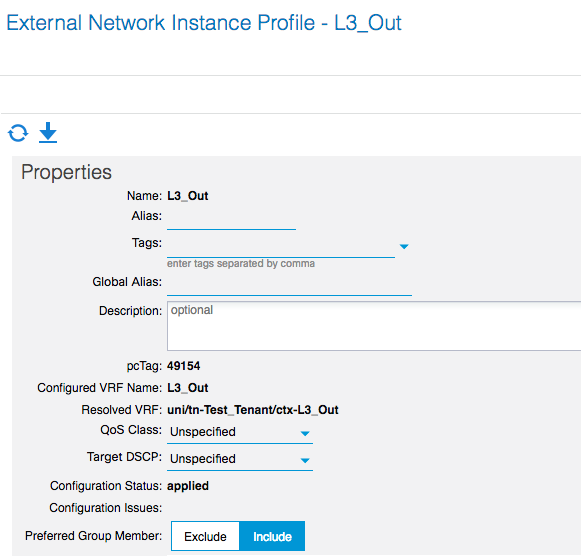
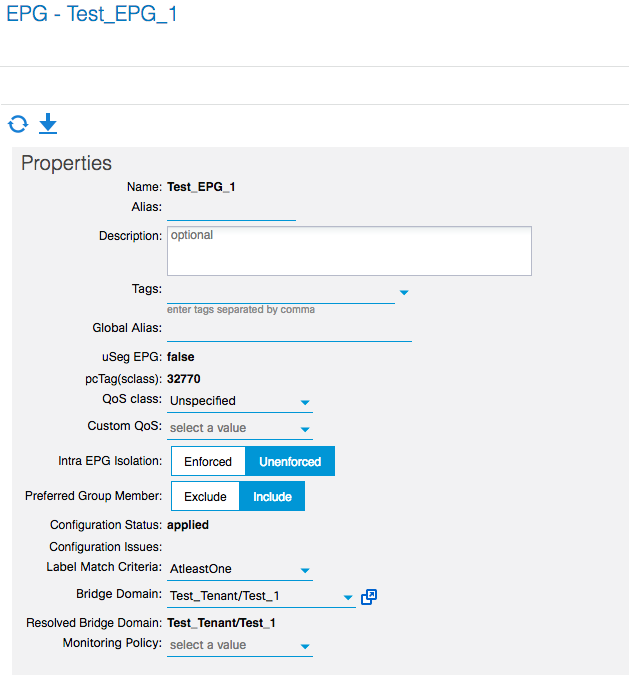
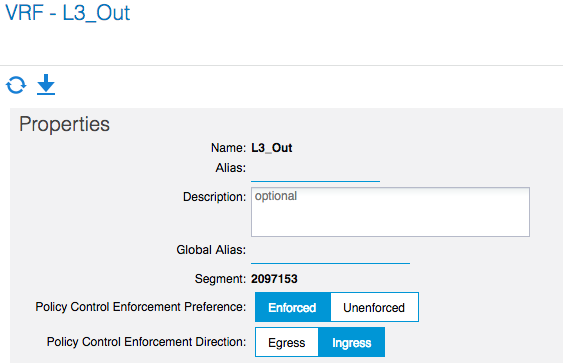
And of course you’ll have to enable the Policy Enforcement in the VRF:
This is how the configuration looks in the CLI
Note the whitelist-blacklist-mix and vrf-blacklist-mode command!
tenant Test_Tenant
vrf context L3_Out
whitelist-blacklist-mix
exit
l3out L3_Out
vrf member L3_Out
exit
bridge-domain Test_1
vrf member L3_Out
exit
bridge-domain Test_2
vrf member L3_Out
exit
application Test_App
epg Test_EPG_1
bridge-domain member Test_1
vmware-domain member ACI_DVS push on-demand
exit
vrf-blacklist-mode
exit
epg Test_EPG_2
bridge-domain member Test_2
vmware-domain member ACI_DVS
exit
vrf-blacklist-mode
exit
exit
external-l3 epg L3_Out l3out L3_Out
vrf member L3_Out
match ip 128.0.0.0/1
match ip 0.0.0.0/1
contract consumer Default_ANY
deny-mode
exit
interface bridge-domain Test_1
ip address 10.11.1.1/24 secondary scope public
exit
interface bridge-domain Test_2
ip address 10.11.2.1/24 secondary scope public
exit
exit
And that’s it. You have connectivity between the members of the Preferred Group with Policy Control Enforcement On and without any contract!
Further infos can be found on Cisco’s TechNotes: Cisco APIC and Contract Preferred Groups